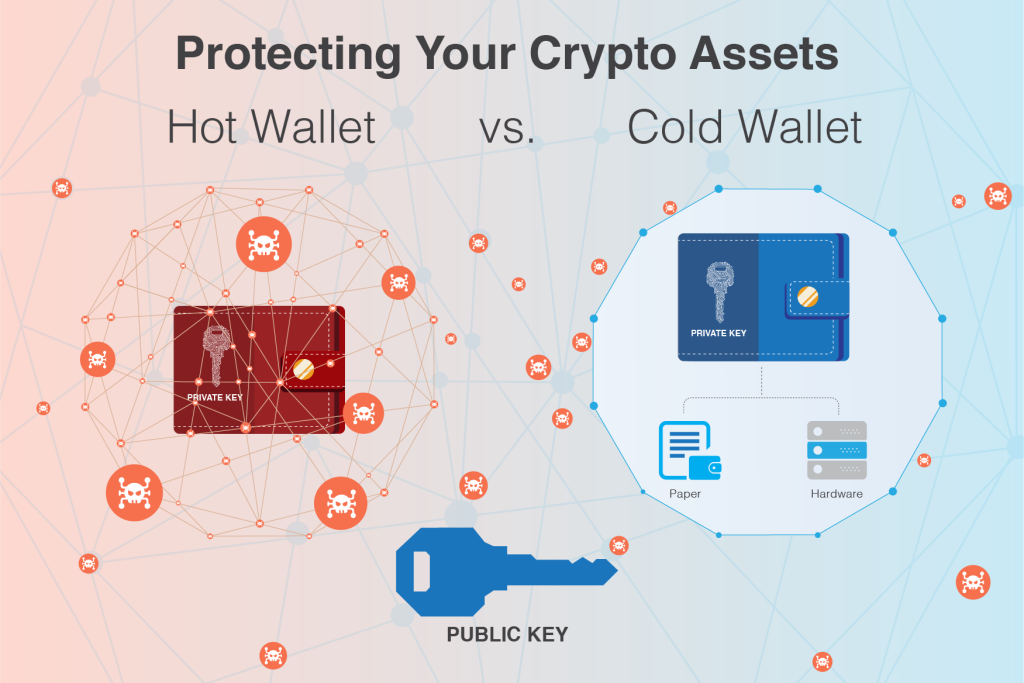
A hot wallet is a type of wallet or purse that is internet-connected and web-based. It is commonly used to store and manage cryptocurrency online. Unlike a cold wallet, which is offline and more secure, a hot wallet is constantly connected to the internet and therefore more susceptible to hacking or theft.
Hot wallets are convenient for quick and easy access to your cryptocurrency. They are typically provided by third-party platforms or exchanges and can be accessed through a web browser or mobile app. However, this convenience comes at a cost – the increased risk of cyber attacks. It is essential to take extra precautions to protect your assets when using a hot wallet.
When using a hot wallet, it is crucial to choose a reputable provider with strong security measures in place. Look for platforms that offer two-factor authentication, encryption, and regular security updates. Additionally, it is advisable to only keep small amounts of cryptocurrency in a hot wallet for everyday transactions and larger amounts in a cold wallet for long-term storage.
In conclusion, a hot wallet is an internet-connected, web-based, online wallet. While it offers convenience and accessibility for managing your cryptocurrency, it is essential to be aware of its security vulnerabilities and take appropriate measures to protect your assets.
Understanding Hot Wallets
In the world of cryptocurrency, a hot wallet refers to an online, internet-connected wallet that allows users to store and manage their crypto assets. Unlike cold wallets, which are offline and more secure, hot wallets are accessible through the web and offer greater convenience and accessibility.
A hot wallet, also known as a web-based or online wallet, functions like a digital purse where users can securely store their cryptocurrencies and perform transactions whenever they need to. With just an internet connection, users can easily access their hot wallets and manage their crypto assets from anywhere in the world.
Hot wallets are particularly popular among active traders and frequent users of cryptocurrencies. Their easy accessibility and ability to quickly execute transactions make them ideal for those who need immediate access to their funds.
However, it’s important to note that hot wallets are connected to the internet, which makes them more vulnerable to hacking attempts and security breaches compared to cold wallets. Users must take extra precautions to ensure the safety of their assets when using hot wallets.
Advantages of Hot Wallets
- Convenient and easy access to crypto assets
- Ability to quickly execute transactions
- Support for multiple cryptocurrencies
- Integration with various web-based services and platforms
- Allowance for seamless cryptocurrency management
Disadvantages of Hot Wallets
- Higher risk of security breaches and hacking attempts
- Potential loss of funds in case of a successful attack
- Dependence on internet connectivity
- Limited control over private keys
Hot wallets can be an excellent choice for users who prioritize accessibility and convenience over absolute security. However, it is crucial to implement additional security measures, such as two-factor authentication and regular backups, to protect against potential threats.
Ultimately, the decision to use a hot wallet or a cold wallet depends on an individual’s specific needs and risk tolerance. It is wise to diversify wallet usage and allocate funds accordingly to maximize the security and accessibility of cryptocurrency assets.
The Importance of Security
In the world of cryptocurrency, security is of paramount importance, especially when it comes to hot wallets. A hot wallet is an online wallet that allows users to store and manage their cryptocurrency through the internet. It is also known as an internet-connected or web-based wallet.
With the rise in popularity of cryptocurrencies, hackers and cybercriminals have become more active in exploiting vulnerabilities in online wallets. This highlights the importance of ensuring the security of your hot wallet.
One of the key risks associated with hot wallets is the potential for hacking and theft. Since hot wallets are connected to the internet, they are more susceptible to attacks. Hackers can exploit vulnerabilities in the wallet’s security measures, gain unauthorized access, and steal the user’s cryptocurrency.
To mitigate these risks, it is crucial to choose a reliable and reputable hot wallet provider. Look for wallets that have a strong track record of security and use industry-standard encryption protocols. Additionally, enable two-factor authentication (2FA) to add an extra layer of security to your wallet.
It is also recommended to regularly update your wallet software to ensure you have the latest security patches. Developers often release updates to address any vulnerabilities that may have been discovered.
Furthermore, it is essential to practice good security hygiene when using a hot wallet. This includes using strong, unique passwords for your wallet and regularly changing them. Avoid sharing your wallet information or private keys with anyone and be cautious of phishing attempts.
In addition to the steps mentioned above, it is advisable to keep only a small amount of cryptocurrency in your hot wallet for day-to-day transactions. The majority of your funds should be stored in a cold wallet, which is offline and not connected to the internet.
By following these security measures, you can significantly reduce the risk of hacking and theft when using a hot wallet for your cryptocurrency transactions. Remember, your wallet is like your online purse, and it is crucial to guard it with the utmost care.
Advantages of Hot Wallets

Hot wallets refer to internet-connected wallets that are accessible through web-based platforms. These wallets are often preferred by individuals who frequently engage in cryptocurrency transactions and require online access to their funds. Here are some advantages of using hot wallets:
-
Convenience: Hot wallets provide a convenient way to store and access cryptocurrencies online. Users can easily log in to their web-based wallet accounts from anywhere with an internet connection, making it easy to manage their funds on the go.
-
Instant Transactions: Hot wallets enable fast and instant transactions. Users can quickly send and receive cryptocurrencies without the need to wait for confirmations from the blockchain network. This makes hot wallets ideal for users who require immediate access to their funds.
-
User-Friendly Interfaces: Hot wallets typically come with user-friendly interfaces that make it easy for users to navigate and manage their funds. These interfaces often include features such as transaction history, balance tracking, and the ability to connect to external exchanges for trading.
-
Accessibility: With hot wallets, users have constant access to their funds as long as they have an internet connection. This accessibility allows users to monitor their balances, make transactions, and react quickly to market movements.
-
Backup and Recovery: Most hot wallets provide options for backing up and recovering wallet data. Users can typically create backups of their wallet’s private keys or mnemonic phrases, which can be used to recover their wallet in case of loss or theft.
In conclusion, hot wallets offer several advantages, including convenience, instant transactions, user-friendly interfaces, accessibility, and backup and recovery options. However, it’s important to note that hot wallets are connected to the internet and may carry some security risks, so users should take appropriate measures to protect their funds.
Disadvantages of Hot Wallets
While hot wallets offer convenience and easy access to your cryptocurrency, they also come with a number of disadvantages:
- Online Storage: Hot wallets are web-based, which means your cryptocurrency is stored online. This makes them more vulnerable to hacking and other cyber attacks.
- Internet Connectivity: Hot wallets require internet connectivity to function properly. If you have a poor internet connection or experience an outage, you may not be able to access your wallet or make transactions.
- Higher Risk: Since hot wallets are web-based and connected to the internet, they are considered to be more exposed to potential security breaches. This makes them a higher risk option compared to offline or cold wallets.
- Limited Control: With hot wallets, you are relying on a third-party provider to secure your cryptocurrency. While many wallet providers have robust security measures in place, you ultimately have less control over the security of your funds compared to offline wallets.
- Potential Loss of Funds: In the event that your hot wallet provider experiences a security breach or goes out of business, there is a risk that you could lose access to your funds. It is important to choose a reputable and trustworthy provider.
It’s important to weigh the advantages and disadvantages of hot wallets before deciding to use one. While they offer convenience and accessibility, it’s crucial to prioritize the security of your cryptocurrency and carefully consider the risks involved.
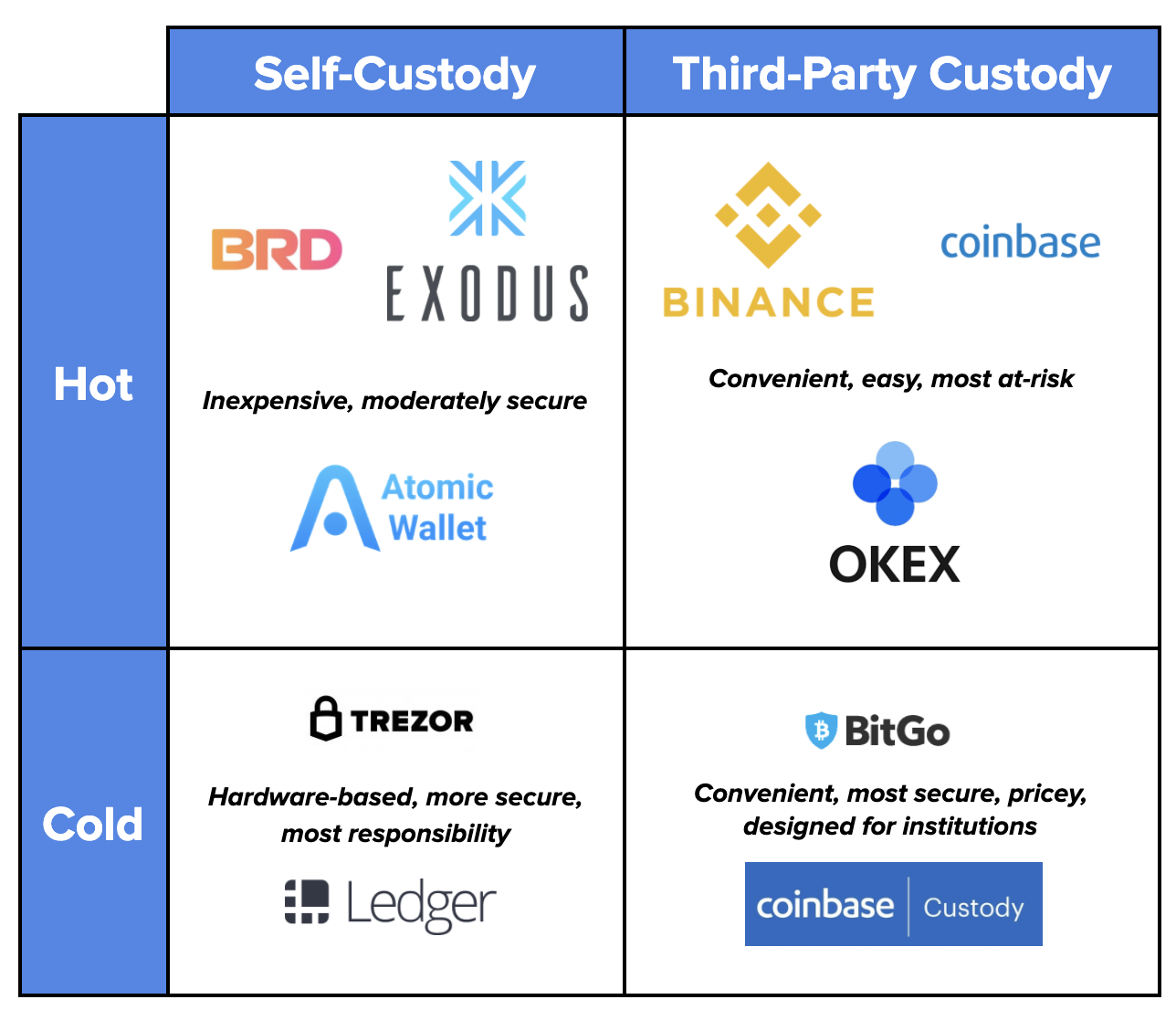
Types of Hot Wallets

Hot wallets are internet-connected wallets that are used for storing and managing cryptocurrency. There are several types of hot wallets available, each with its own features and benefits.
Web-based Wallets
Web-based wallets, also known as online wallets, are hot wallets that are accessible through a web browser. These wallets are typically provided by cryptocurrency exchanges or third-party wallet providers. Users can access their wallet by logging into their account on the website. Web-based wallets are convenient and easy to use, but they are also more susceptible to hacking and online attacks compared to other types of wallets.
Mobile Wallets
Mobile wallets are hot wallets that are installed on a mobile device, such as a smartphone or tablet. These wallets are convenient for people who frequently use their mobile devices for cryptocurrency transactions. Mobile wallets often have additional features, such as QR code scanning, which makes it easier to send and receive cryptocurrency. However, mobile wallets also run the risk of being lost or stolen if the mobile device is lost or compromised.
Desktop Wallets
Desktop wallets are hot wallets that are installed and run on a desktop computer or laptop. These wallets provide a higher level of security compared to web-based or mobile wallets, as they are not connected to the internet all the time. Desktop wallets are only accessible from the specific device that they are installed on, which reduces the risk of hacking or online attacks. However, desktop wallets can still be vulnerable to malware or viruses.
Hardware Wallets
Hardware wallets are physical devices that are specifically designed for storing cryptocurrency. These wallets store the user’s private keys offline, away from the internet, which provides the highest level of security. Hardware wallets are usually small, portable devices that can be connected to a computer or mobile device when needed. Although hardware wallets offer excellent security, they can be more expensive compared to other types of hot wallets.
Summary
Hot wallets are a popular choice for cryptocurrency users who require frequent access to their funds. Web-based, mobile, desktop, and hardware wallets are all types of hot wallets that offer different levels of convenience and security. It is important for users to carefully consider their needs and conduct thorough research before choosing a hot wallet for storing their cryptocurrency.
Web-based Crypto Wallets

Web-based crypto wallets, also known as online or hot wallets, are cryptocurrency purses that operate through internet-connected devices. These wallets allow users to store, manage, and transact with their cryptocurrencies online.
Unlike hardware wallets or paper wallets, web-based wallets are accessible through a web browser, making them convenient for everyday use. They eliminate the need to download and install specialized software, as everything is done through a web interface.
Web-based wallets store the user’s private keys online, which means they are potentially at risk of being hacked. Therefore, it is important to choose a reputable and secure web-based wallet provider.
One advantage of web-based wallets is their accessibility. Users can access their funds from any internet-connected device, whether it’s a computer, smartphone, or tablet. This makes it easy for users to monitor their cryptocurrency holdings and carry out transactions on the go.
Another advantage is the ability to integrate with various cryptocurrency exchanges and services. Web-based wallets often have built-in features that allow users to buy, sell, and exchange cryptocurrencies directly within the wallet interface.
Some web-based wallets offer additional security measures, such as two-factor authentication, to protect against unauthorized access. It is recommended to enable these features when available to enhance the security of the wallet.
However, as with any online service, web-based wallets are not without risks. Users must be cautious of phishing attempts, malware, and other online threats that could compromise their wallet and funds. It is important to keep the device used to access the wallet secure and up to date with the latest security patches.
In summary, web-based crypto wallets are online wallets that allow users to store, manage, and transact with their cryptocurrencies through internet-connected devices. They offer convenience and accessibility but require careful consideration of security measures to protect against potential risks.
Online Cryptocurrency Wallets
Online cryptocurrency wallets, also known as web-based wallets, are internet-connected wallets that allow users to store and manage their crypto assets online. These wallets provide a convenient way for individuals to access and transact with their cryptocurrencies without the need for a physical wallet.
Unlike hardware wallets or paper wallets, which store crypto keys offline, online wallets are internet-connected and accessible through a web browser. This accessibility makes them particularly convenient for users who frequently need to access their crypto assets or make transactions online.
Purpose of Online Wallets
The primary purpose of online wallets is to provide a secure and user-friendly solution for storing and managing cryptocurrencies. With an online wallet, users can access their crypto assets from any internet-connected device, such as a computer, smartphone, or tablet.
Online wallets also often provide additional features to enhance the user experience, such as integration with popular crypto exchanges, the ability to track portfolio performance, and the option to buy or sell cryptocurrencies directly within the wallet.
Benefits and Risks
There are several benefits and risks associated with using online wallets for storing cryptocurrencies:
- Convenience: Online wallets offer easy accessibility and allow users to manage their crypto assets from anywhere with an internet connection.
- Integration: Many online wallets integrate with popular crypto exchanges, making it seamless to trade or exchange cryptocurrencies within the wallet.
- Security: While online wallets employ various security measures to protect user funds, they are still susceptible to online threats, such as hacking or phishing attacks.
- Risk of loss: In the event of a security breach or if the online wallet provider goes out of business, there’s a risk of losing access to the wallet and the associated crypto assets.
Choosing an Online Wallet
When selecting an online wallet, it’s crucial to consider the wallet’s security features, reputation, customer support, and the cryptocurrencies it supports. Users should also research potential wallet providers to ensure they have a reliable track record and take appropriate security measures to protect user funds.
Additionally, it’s advisable to use additional security measures, such as enabling two-factor authentication and using strong, unique passwords, to further enhance the security of the online wallet.
| Pros | Cons |
|---|---|
| Easy accessibility | Potential security risks |
| Integration with exchanges | Risk of loss |
| User-friendly features |
Internet-connected Crypto Purses
Internet-connected crypto purses, also known as hot wallets, are online or web-based wallets that allow users to store and manage their cryptocurrencies. These wallets are connected to the internet and provide quick and convenient access to cryptocurrency holdings.
Advantages of Internet-connected Crypto Purses
- Convenience: Internet-connected crypto purses can be accessed from any internet-connected device, providing users with the flexibility to manage their cryptocurrencies on-the-go.
- Easy transactions: These wallets enable users to quickly send and receive cryptocurrencies, making it convenient for everyday use or trading.
- Multiple cryptocurrency support: Many internet-connected wallets support a wide range of cryptocurrencies, allowing users to manage multiple digital assets in one place.
- Regular updates: Web-based wallets are often regularly updated by their developers, ensuring the latest security features and bug fixes are implemented.
Security Considerations
While internet-connected crypto purses offer convenience, they also come with security considerations:
- Online vulnerability: Hot wallets are connected to the internet, making them potentially vulnerable to hacking attempts or malware attacks.
- Third-party risk: These wallets are typically managed by a third-party provider, meaning users need to trust the provider’s security measures and policies.
- Phishing attacks: Hackers can impersonate web-based wallets, attempting to trick users into revealing their login credentials or transferring their cryptocurrencies to fraudulent addresses.
Best Practices for Secure Usage
To ensure the security of your internet-connected crypto purse, it is recommended to follow these best practices:
- Choose a reputable wallet provider with a proven track record in security.
- Enable two-factor authentication (2FA) to add an extra layer of security to your account.
- Regularly update your wallet software to benefit from the latest security patches and enhancements.
- Use unique and strong passwords for your wallet account.
- Be cautious of phishing attempts and only access your wallet through the official website or app.
| Wallet Name | Features | Supported Cryptocurrencies | Security Measures |
|---|---|---|---|
| Wallet A | Easy-to-use interface, multi-factor authentication | Bitcoin, Ethereum, Litecoin | Encrypted private keys, cold storage for funds |
| Wallet B | Mobile app, transaction history | Bitcoin, Ripple, Stellar | Biometric authentication, transaction verification |
| Wallet C | Integrated exchange, portfolio tracking | Bitcoin, Ethereum, Bitcoin Cash | Two-factor authentication, hardware wallet integration |
Remember, when using internet-connected crypto purses, it is essential to prioritize security and employ best practices to protect your cryptocurrency holdings.
Key Security Considerations
When using an online, internet-connected hot wallet for storing and managing your cryptocurrency, it is important to consider the following key security considerations:
1. Web-based Wallet
A hot wallet is a web-based wallet that allows you to access and manage your crypto assets through a web browser. As such, it is important to ensure that you use a reputable and secure web-based wallet provider that has implemented strong security measures for protecting your funds.
2. Strong Password
Creating a strong password is crucial when using a hot wallet. Make sure to use a combination of letters, numbers, and special characters and avoid using easily guessable information such as your name or birthdate. Additionally, consider using a password manager to securely store and generate complex passwords.
3. Two-Factor Authentication
Enable two-factor authentication (2FA) for an added layer of security. This will require you to provide an additional piece of information, typically a code sent to your mobile device, when logging into your hot wallet. It helps protect against unauthorized access even if your password is compromised.
4. Regular Updates
Ensure that your hot wallet software is regularly updated. Wallet providers often release updates that include security patches and bug fixes, so it is important to keep your wallet up to date to ensure the highest level of security.
5. Secure Connection
When accessing your hot wallet, make sure to use a secure internet connection. Avoid using public Wi-Fi networks or unsecured connections that may expose your sensitive information to potential hackers. Consider using a VPN (Virtual Private Network) for an added layer of encryption.
6. Backup and Recovery

Regularly backup your hot wallet and store the backup in a secure location. This backup will allow you to recover your wallet and funds in case of device loss, damage, or theft. Make sure to follow the backup instructions provided by your wallet provider.
7. Strong Security Practices
Adopt strong security practices such as keeping your operating system and antivirus software up to date, being cautious when clicking on suspicious links or downloading unknown software, and regularly monitoring your wallet transactions for any unauthorized activity.
By considering these key security considerations, you can enhance the security of your online crypto wallet and reduce the risk of unauthorized access or loss of funds.
Tips for Safely Using Hot Wallets
Hot wallets are online, internet-connected wallets that allow you to store and manage your cryptocurrency. While convenient, they also come with their own security risks. To help you safely use hot wallets, here are some tips:
1. Choose a reputable and secure hot wallet
When selecting a hot wallet, make sure to choose one from a reputable provider that has a strong track record of security. Look for wallets that have features like two-factor authentication and multi-signature functionality to enhance the security of your crypto.
2. Keep software and devices updated
Regularly update both your hot wallet software and the devices you use to access it. This ensures that you have the latest security patches and fixes, reducing the risk of vulnerabilities that could be exploited by hackers.
3. Use a unique and strong password
Create a unique and strong password for your hot wallet that is not used for any other online accounts. A strong password should be a combination of upper and lower case letters, numbers, and special characters.
4. Enable two-factor authentication
Two-factor authentication adds an extra layer of security by requiring a code from a second device or app in addition to your password. Enable this feature on your hot wallet to prevent unauthorized access.
5. Be cautious of phishing attempts
Be wary of any emails or messages that request your hot wallet login credentials or personal information. Always verify the source of the communication and never click on suspicious links. Hackers often use phishing attempts to trick users into revealing their login information.
6. Keep a backup of your wallet
Regularly back up your hot wallet and store the backup in a secure location. This will ensure that you can recover your crypto in case of theft, loss, or hardware failure.
7. Only keep small amounts in your hot wallet
To minimize the potential loss in case of a security breach, only keep small amounts of cryptocurrency in your hot wallet. Consider using a cold wallet for storing larger amounts of crypto.
8. Educate yourself about security best practices
Stay informed about the latest security best practices for using hot wallets. Educate yourself about the risks and how to mitigate them. This will help you make informed decisions and protect your cryptocurrency.
By following these tips, you can enhance the security of your hot wallet and minimize the risks associated with online crypto storage.
Final Thoughts

In today’s digital age, owning a cryptocurrency is common and having a secure way to store it is crucial. Hot wallets provide a convenient and easy-to-use option for managing your crypto assets.
However, it’s important to remember that hot wallets are web-based and internet-connected, making them vulnerable to potential security threats. While there are measures in place to protect your crypto, it’s essential to stay vigilant and take precautions to keep your funds safe.
When choosing a hot wallet, it’s imperative to select a reputable one that has implemented industry-standard security features. Additionally, regularly updating your wallet’s software and using strong passwords can add an extra layer of security.
While hot wallets offer online convenience, it’s always advisable to keep only a small percentage of your total cryptocurrency holdings in them. For larger amounts, consider utilizing cold storage options such as hardware wallets.
In conclusion, hot wallets are an excellent choice for quick and easy access to your crypto assets. However, they come with inherent risks due to their online nature. By taking the necessary precautions and being cautious, you can maximize the security of your online cryptocurrency purse.
Frequently Asked Questions:
What is a hot wallet in cryptocurrency?
A hot wallet in cryptocurrency refers to an online wallet that is connected to the internet. It allows users to access their digital assets and make transactions quickly and easily.
What are the advantages of using a hot wallet?
One advantage of using a hot wallet is the convenience it offers. You can access your funds from anywhere with an internet connection. Additionally, hot wallets are usually user-friendly and have features like multi-currency support and easy integration with exchanges.
Are hot wallets safe?
Hot wallets are generally considered less secure than cold wallets because they are connected to the internet and are therefore more vulnerable to hacking attempts. However, reputable hot wallet providers implement strong security measures such as encryption, two-factor authentication, and regular security audits to protect users’ funds.
Can I store all types of cryptocurrencies in a hot wallet?
Most hot wallets support a wide range of cryptocurrencies, including popular ones like Bitcoin, Ethereum, and Litecoin. However, it’s important to check the wallet’s website or documentation to ensure that the specific cryptocurrencies you want to store are supported.
Can I use a hot wallet for long-term storage of cryptocurrencies?
Hot wallets are primarily designed for easy and quick access to funds, making them more suitable for daily transactions and frequent trading. For long-term storage, it is generally recommended to use a cold wallet, which is offline and provides greater security against hacking attempts.
What are some popular hot wallet providers?
Some popular hot wallet providers include Coinbase Wallet, MetaMask, MyEtherWallet, and Trust Wallet. These wallets have user-friendly interfaces, good security features, and support for multiple cryptocurrencies.
Videos:
Ripple Wins for Crypto, Undercutting SEC, Can Bitcoin or Crypto Breakout – Caffeine & Crypto – 7/15
Top 3 Cold Wallets! (Best Places to HODL Bitcoin!)

What are some of the reputable providers that offer strong security measures for hot wallets?
Some reputable providers that offer strong security measures for hot wallets are Coinbase, Binance, and Trezor. They have implemented stringent security protocols such as two-factor authentication, encryption, and regular security updates to ensure the safety of your digital assets. It’s always a good idea to do your own research and read reviews before choosing a hot wallet provider, as security is paramount in the cryptocurrency world.
Hot wallets are great for accessing cryptocurrencies conveniently, but it’s important to remember the increased risk of cyber attacks. Make sure to choose a reputable provider and take extra precautions to protect your digital assets.
I have been using a hot wallet for quite some time now and I must say, it has made managing my cryptocurrencies so much easier. Being able to access my assets from any device is a great convenience. However, I do understand the risks involved. That’s why I always make sure to choose a provider with strong security measures. Safety should always be a top priority when it comes to managing digital assets.
Hot wallets are a great way to easily access and manage cryptocurrency on the go. However, it is important to be cautious and take extra steps to protect your assets from potential cyber attacks. Always choose a reliable provider with strong security measures in place.
What measures can users take to ensure the security of their assets while using a hot wallet?
Hi AnnaSmith, when using a hot wallet, it is important for users to follow certain measures to ensure the security of their assets. Firstly, choose a reputable and trusted provider that offers strong security measures such as two-factor authentication and encryption. Regularly update both your hot wallet and device to ensure you have the latest security patches. Avoid using public Wi-Fi networks when accessing your hot wallet and always use a strong, unique password. Lastly, consider diversifying your assets and using a hot wallet for everyday transactions, while keeping larger amounts in a cold wallet for long-term storage. Stay safe and happy trading!
I think hot wallets are a great option for storing and managing cryptocurrencies online. They provide easy access and convenience, allowing users to make transactions from any device with an internet connection. However, it is important to be cautious and take extra security measures to protect your assets. I personally use a hot wallet for everyday transactions and keep larger amounts in a cold wallet for long-term storage.
I personally think that hot wallets are very convenient for daily transactions. They provide quick and easy access to cryptocurrencies from any device with an internet connection. However, it’s crucial to choose a reputable provider and take extra precautions to ensure the security of your assets. Overall, I find hot wallets to be a practical solution for managing cryptocurrencies online.
Is there any way to completely eliminate the risk of hacking or theft when using a hot wallet? What measures can users take to ensure maximum security?
While it is difficult to completely eliminate the risk of hacking or theft when using a hot wallet, there are several measures that users can take to enhance security. Firstly, enable two-factor authentication (2FA) for your hot wallet, which adds an extra layer of protection by requiring a verification code in addition to a password. Additionally, regularly update your wallet software to ensure that you have the latest security patches and features. It is also recommended to use a unique and strong password for your hot wallet, one that is not used for any other accounts. Lastly, consider using hardware wallets for storing larger amounts of cryptocurrency, as they provide an offline and more secure storage solution. Remember, a combination of these measures can greatly reduce the risk of hacking or theft, but it’s always important to stay vigilant and keep up with the latest security practices.
I’ve been using a hot wallet for a while now and it’s been really convenient for managing my cryptocurrencies. Although I understand that it may have some security risks, I make sure to choose a provider with strong security measures and only keep small amounts of cryptocurrency in it. Overall, it’s a great solution for easy access to my digital assets.
I think using a hot wallet can be a convenient option for accessing and managing cryptocurrencies online. However, it’s crucial to prioritize security and choose a reputable provider with strong security measures in place. Regular security updates and two-factor authentication are a must! Always make sure to keep larger amounts in a cold wallet for long-term storage.
I personally prefer using a hot wallet for quick and easy access to my cryptocurrencies. The convenience of being able to make transactions from any device with internet connection outweighs the potential risks. As long as I take necessary security precautions, such as choosing a reputable provider and keeping small amounts of cryptocurrency in the hot wallet, I feel confident in using it for my everyday transactions.
I have been using a hot wallet for a while now, and it has definitely made managing my cryptocurrencies more convenient. I can access my assets from any device with an internet connection and make quick transactions. However, I do agree that the increased risk of cyber attacks is a concern. That’s why I always make sure to choose a reputable provider with strong security measures in place.
A hot wallet is really convenient for quick access to your cryptocurrency, but you need to be cautious about the security risks. Make sure to choose a reputable provider and take extra precautions to protect your assets.
Hot wallets are really convenient for quick and easy access to your cryptocurrency. However, we must be cautious and take necessary security measures to protect our assets. It’s always a good idea to keep larger amounts in a cold wallet.
Can you please provide some examples of reputable hot wallet providers that offer strong security measures?
Sure, Emma45! Here are a few examples of reputable hot wallet providers that offer strong security measures:
1. Coinbase Wallet: Coinbase is a well-established cryptocurrency exchange that offers a hot wallet solution with advanced security features.
2. Ledger Live: Ledger Live is a popular hot wallet provider known for its robust security measures, including secure chip technology.
3. Mycelium Wallet: Mycelium is a mobile hot wallet that prioritizes security and privacy with features like HD encryption and local storage.
Remember to always do your own research and choose a provider that aligns with your individual security needs. Stay safe!
I strongly believe that using a hot wallet for managing cryptocurrencies is a convenient solution. With easy access from any device and quick transactions, it makes cryptocurrency management a breeze. However, it’s important to stay vigilant and choose a reliable provider with robust security measures to protect your assets from potential cyber attacks.
Hot wallets are really convenient for everyday transactions and quick access to my cryptocurrency. I always make sure to choose a reputable provider with strong security measures to keep my assets safe. However, I do keep larger amounts in a cold wallet for long-term storage just to be extra cautious.
I have been using a hot wallet for a while now and it has been very convenient. I can easily access my cryptocurrencies from any device with an internet connection. However, I also understand the risks involved, so I always make sure to choose a reputable provider with strong security measures in place. It’s all about finding the right balance between convenience and security.
I personally find hot wallets to be very convenient for managing my cryptocurrencies on-the-go. With a hot wallet, I can easily access my digital assets from any device with an internet connection and make quick transactions. However, it’s important to stay vigilant and choose a reliable provider with robust security features to protect against potential cyber threats.
Hot wallets are great for easy access to your cryptocurrency. However, it’s important to be cautious and choose a reliable provider with top-notch security measures. Encrypting our digital assets and keeping only small amounts in a hot wallet can help protect against cyber attacks. Stay safe and crypto on!
I have been using a hot wallet for a while now, and it’s been so convenient for quick transactions. However, I always make sure to keep only small amounts of cryptocurrency in it and store larger amounts in a cold wallet for security purposes.
I’ve been using a hot wallet for a while now, and I find it very convenient for accessing my cryptocurrencies on the go. However, I do agree that security is a major concern with hot wallets. That’s why I make sure to choose a trusted provider with strong security measures in place. It’s all about finding the right balance between convenience and safety.
I’ve been using a hot wallet for a while now and it’s been really convenient. Being able to access my cryptocurrencies from any device is a game-changer. However, I do understand the increased risk of cyber attacks, so I make sure to take extra security measures. It’s important to choose a trusted provider and keep only small amounts of cryptocurrency in the hot wallet for everyday transactions. Overall, it’s a great solution for managing my digital assets online.
Is a hot wallet safe to use? What are the security measures that should be taken?
A hot wallet can be safe to use if you take the necessary security measures. When using a hot wallet, it’s important to choose a reputable provider that offers strong security measures such as two-factor authentication, encryption, and regular security updates. Additionally, you should only keep small amounts of cryptocurrency in a hot wallet for everyday transactions and store larger amounts in a cold wallet for long-term security. By following these precautions, you can minimize the risk of cyber attacks and protect your assets.
I have been using a hot wallet for a while now and I find it really convenient. Being able to access my cryptocurrencies from any internet-connected device is great. However, I do worry about the security risks. I make sure to choose a reputable provider and take all necessary precautions to protect my assets. Overall, hot wallets are a useful solution for managing cryptocurrencies online.
I personally find hot wallets to be a convenient option for managing cryptocurrencies online. With easy access from any device, it makes transactions hassle-free. However, the increased risk of cyber attacks makes it crucial to choose a reliable provider with strong security measures in place.
I personally prefer using a hot wallet for its convenience. Being able to access my cryptocurrencies from any device is incredibly useful. Of course, security is a concern, but as long as I take the necessary precautions, I feel confident in using a hot wallet.
What are some reputable providers for hot wallets with strong security measures? I want to make sure my assets are protected.
Hi JohnDoe123, there are several reputable providers for hot wallets with strong security measures. Some popular options include Coinbase, Binance, and Kraken. These platforms have robust security features such as two-factor authentication, encryption, and regular security updates. Make sure to do your research and choose a platform that best suits your needs and provides the level of security you are comfortable with. Happy investing!
Is it really safe to store and manage cryptocurrency online with a hot wallet? What measures are in place to protect against hacking or theft?
Yes, storing and managing cryptocurrency online with a hot wallet can be safe if you take the necessary precautions. Reputable providers have strong security measures in place such as two-factor authentication, encryption, and regular security updates. However, it is always advisable to only keep small amounts of cryptocurrency in a hot wallet for everyday transactions and larger amounts in a cold wallet for long-term storage. This way, you can minimize the risk of hacking or theft.
Yes, it is relatively safe to store and manage cryptocurrency online with a hot wallet if you take the necessary precautions. Reputable providers usually have strong security measures such as two-factor authentication, encryption, and regular security updates to protect against hacking or theft. However, it is important to keep in mind that hot wallets are more susceptible to cyber attacks compared to cold wallets. It is advisable to only keep small amounts of cryptocurrency in a hot wallet for everyday transactions and larger amounts in a cold wallet for long-term storage.
Is it safe to use a hot wallet for storing large amounts of cryptocurrency?
It’s generally not recommended to store large amounts of cryptocurrency in a hot wallet due to the increased risk of cyber attacks. Hot wallets are more susceptible to hacking or theft since they are constantly connected to the internet. It’s safer to use a cold wallet for storing larger amounts of cryptocurrency for long-term security.
What are some recommended platforms for hot wallets with strong security measures?
When it comes to hot wallets with strong security measures, I would recommend checking out platforms such as Coinbase, Ledger, and Trust Wallet. These platforms offer features like two-factor authentication, encryption, and regular security updates to ensure the safety of your digital assets. Just remember to always do your own research and choose a platform that best fits your needs. Stay safe!
Hot wallets are a great option for users who need quick and easy access to their cryptocurrency. I’ve been using a hot wallet for a while now and it’s been very convenient. However, I always make sure to take extra precautions like using strong passwords and enabling two-factor authentication to protect my assets. Overall, I think hot wallets provide a secure solution for managing cryptocurrencies online.
Can hot wallets really provide a secure solution for storing and managing cryptocurrencies online? I’ve heard that they are more susceptible to hacking or theft. What extra precautions can be taken to protect assets when using a hot wallet?
Yes, hot wallets can provide a secure solution for storing and managing cryptocurrencies online. While it is true that hot wallets are more susceptible to hacking or theft compared to cold wallets, there are extra precautions you can take to protect your assets. Firstly, choose a reputable provider with strong security measures such as two-factor authentication and regular security updates. Secondly, regularly update your wallet software to keep up with the latest security enhancements. Lastly, consider keeping only small amounts of cryptocurrency in your hot wallet for everyday transactions and store larger amounts in a cold wallet for long-term storage. By following these precautions, you can minimize the risks associated with using a hot wallet.
I have been using hot wallets for a while now and I find them extremely convenient for quick access to my cryptocurrency. However, I always make sure to keep only small amounts of crypto in my hot wallet and store the larger amounts in a cold wallet for added security. It’s important to choose a reputable provider with strong security measures to minimize the risk of hacking or theft.
I really like using hot wallets for my cryptocurrency. It’s so convenient to be able to access it from any device with an internet connection. However, I always make sure to take the necessary security precautions to keep my assets safe.
A hot wallet is definitely more convenient for quick and easy access to your cryptocurrency. However, one should always be cautious and choose a reputable provider with strong security measures. It is better to keep larger amounts in a cold wallet for long-term storage to minimize the risk of hacking or theft.
I’ve been using a hot wallet for a while now and I find it very convenient. It allows me to access my cryptocurrencies anytime and anywhere. However, I do understand the risks involved, so I always make sure to use a reputable provider and take extra precautions to protect my assets. Overall, I think a hot wallet is a great solution for managing cryptocurrencies online.
Is it safe to store large amounts of cryptocurrency in a hot wallet? How can I ensure the security of my assets?
Storing large amounts of cryptocurrency in a hot wallet can be risky. Since hot wallets are constantly connected to the internet, they are more vulnerable to hacking or theft. To ensure the security of your assets, it is advisable to keep larger amounts of cryptocurrency in a cold wallet, which is offline and more secure. A hot wallet can be used for everyday transactions and small amounts of cryptocurrency. Remember to choose a reputable hot wallet provider that offers strong security measures such as two-factor authentication and encryption. Stay safe!
I personally prefer using a hot wallet for my cryptocurrency. It provides me with quick and easy access to my assets, which is important for my daily transactions. I make sure to choose a reliable provider that prioritizes security and regularly updates their systems to protect my funds. Of course, I also take extra precautions by keeping larger amounts in a cold wallet for long-term storage. Overall, using a hot wallet has been convenient and secure for me.
I personally prefer using a hot wallet for its convenience. It allows me to access my cryptocurrencies easily from any device, making transactions a breeze. Of course, I understand the potential risks, but with proper security measures in place, it’s a great solution for managing my digital assets online.
Is it safe to use a hot wallet for long-term storage of large amounts of cryptocurrency?
Using a hot wallet for long-term storage of large amounts of cryptocurrency is not recommended. Hot wallets are more susceptible to hacking or theft due to their constant connection to the internet. It is advisable to use a cold wallet for long-term storage as it provides offline security. Keep your large amounts of cryptocurrency in a cold wallet and use the hot wallet for everyday transactions only.
I completely agree with the article. Using a hot wallet for quick access to my cryptocurrencies is so convenient. However, I always make sure to follow the security recommendations and keep only small amounts in my hot wallet. Safety first!
Hot wallets are a great option for easy access to cryptocurrencies. I use one for my daily transactions and keep larger amounts in a cold wallet for security. It’s important to choose a reliable provider and take extra precautions to protect your assets.
I personally prefer using a hot wallet for my cryptocurrency because of its convenience. Being able to access my assets from any device with an internet connection makes it really easy for me to manage my transactions. Of course, I understand the security risks involved, so I always make sure to choose a reputable provider and take extra precautions to protect my assets. Overall, a hot wallet is a great solution for storing and managing cryptocurrencies online.
Do hot wallets have any additional security features to protect against cyber attacks?
Yes, hot wallets often provide additional security features to protect against cyber attacks. Reputable providers offer two-factor authentication, encryption, and regular security updates to ensure the safety of your digital assets. However, it is still important to take extra precautions and only keep small amounts of cryptocurrency in a hot wallet for everyday transactions. For larger amounts, consider using a cold wallet for long-term storage.
I have been using a hot wallet for a while now and it’s been really convenient for managing my cryptocurrencies. However, I make sure to take all the necessary security precautions to protect my assets. It’s important to choose a trusted provider and keep only small amounts of cryptocurrency in the hot wallet for daily transactions.
I really like using a hot wallet for my cryptocurrencies. It’s so convenient to be able to access my assets from any device with an internet connection. Though I know it’s more susceptible to hacking, I always make sure to choose a reputable provider with strong security measures. So far, it’s been a great solution for managing my digital assets online.
A hot wallet is very convenient for managing smaller amounts of cryptocurrency for everyday transactions. However, it’s important to be cautious and choose a reputable provider with strong security measures in place to protect your assets from cyber attacks.
I think using a hot wallet is very convenient for managing my cryptocurrencies on the go. However, I also understand the risks involved with constantly being connected to the internet. It’s important to choose a trustworthy provider and take extra precautions to protect my assets.
Hot wallets are a great option for accessing your cryptocurrencies quickly and conveniently. However, it is important to be cautious and take extra security measures to protect your assets. Always choose a reputable provider with strong security features. Stay safe!
Could you please explain more about the security measures that should be taken when using a hot wallet? Are there any particular platforms you recommend?
Hi Megan23, when using a hot wallet, there are several security measures that you should consider. First, it is crucial to choose a reputable provider that offers strong security features, such as two-factor authentication and encryption. Some platforms that have a good reputation in the industry include Coinbase, Binance, and Ledger. Additionally, make sure to regularly update your hot wallet’s software to patch any potential vulnerabilities. It is also advisable to use a unique and complex password for your hot wallet and enable any available security features, like biometric authentication. Lastly, consider enabling notifications or alerts for any suspicious activities on your hot wallet account. Stay vigilant and regularly monitor your wallet’s activity. Remember, it’s always better to be safe than sorry!
I think using a hot wallet for everyday transactions is a convenient option. However, it’s important to choose a trustworthy provider and take extra precautions to protect your assets. Regular security updates and strong security measures are a must to minimize the risk of hacking or theft.
Hot wallet crypto provides easy access to cryptocurrencies but it’s important to be cautious about the security risks involved. Make sure to choose a reliable provider with robust security features to safeguard your digital assets.
I believe that using a hot wallet for cryptocurrency transactions can offer great convenience due to easy accessibility, but it’s crucial to remain vigilant about security risks. It’s important to choose a trusted provider with strong security features and keep larger amounts in cold storage for added protection.
As an avid cryptocurrency investor, I believe that using a hot wallet for quick access to my assets is convenient but comes with inherent risks. It’s crucial to prioritize security when choosing a provider and to limit the amount stored in a hot wallet to mitigate potential cyber threats. Stay vigilant and take necessary precautions to safeguard your digital assets.
Hot wallets are indeed convenient for easy access to cryptocurrencies, but users must always be mindful of the security risks associated with them. It’s crucial to choose a reputable provider and take necessary precautions to safeguard your digital assets.
Do hot wallets really offer enough security for storing larger amounts of cryptocurrency? How can users ensure their assets are protected from potential cyber attacks?
Hey EmilyCryptoFan21, while hot wallets provide convenient access to cryptocurrencies, they are indeed more vulnerable to cyber attacks compared to cold wallets. To ensure the security of larger amounts of cryptocurrency, users should consider using a combination of hot and cold wallets. By keeping only small amounts in a hot wallet for daily transactions and storing larger sums in a cold wallet offline, users can significantly reduce the risk of potential theft or hack. It’s all about finding the right balance between convenience and security when managing your digital assets. Stay safe out there!
I believe that hot wallets can provide convenient access to cryptocurrencies, but it’s crucial to be cautious due to the increased vulnerability to cyber attacks. Users should choose a reputable provider with strong security measures and consider only keeping small amounts in hot wallets for everyday transactions.
Hot wallets are definitely convenient for easy access to your cryptocurrency, but one must always prioritize security when using them. Make sure to choose a reputable provider with strong security features to protect your digital assets. It’s wise to keep larger amounts in a cold wallet for added safety.
I believe that hot wallets are indeed convenient for quick access to cryptocurrency but the security risks associated with them can’t be ignored. It’s crucial to choose a reputable provider with strong security measures and take extra precautions to safeguard your assets when using a hot wallet.
As someone who values convenience, I can see the appeal of hot wallets for accessing cryptocurrencies easily. However, the security risks associated with constant internet connection are concerning. It’s crucial to prioritize safety and choose a reliable provider with robust security features in place.
Hot wallets provide easy access to your cryptocurrency assets, but it’s vital to remain vigilant against cyber threats. Choose a trusted provider with robust security features and consider keeping smaller amounts in your hot wallet for daily transactions. Safety first!
Using a hot wallet can provide convenient access to cryptocurrencies, but one must stay vigilant against cyber threats. It is important to choose a reliable platform with robust security features to safeguard your digital assets. Keeping larger amounts in a cold wallet for long-term storage is advisable for added protection.
Hot wallets are indeed very convenient for quick access to cryptocurrencies, but users must remain vigilant against cyber threats. It’s crucial to opt for reputable providers with advanced security features like two-factor authentication and encryption to safeguard your digital assets effectively.
Hot wallet crypto provides convenient access to digital assets online, but users should prioritize security when choosing a provider. Two-factor authentication and encryption are essential for protecting your cryptocurrency from cyber attacks.
Hot wallets are definitely convenient for easy access to your cryptocurrency, but it’s crucial to prioritize security. Always choose a reputable provider with strong security measures in place to protect your digital assets from cyber threats.
Could you provide examples of reputable providers that offer strong security measures for hot wallets?
Sure, AlexisJohnson! Some reputable providers known for offering strong security measures for hot wallets include Ledger Nano S, Trezor, and Coinbase. These platforms prioritize security features like two-factor authentication, encryption, and regular security updates to ensure the safety of your digital assets. Remember to research and choose a provider that aligns with your security preferences.
Do hot wallets provide any additional protection against potential cyber threats compared to cold wallets?
Hot wallets do not provide additional protection compared to cold wallets; in fact, they are more susceptible to cyber threats due to their constant internet connection. It is crucial to be vigilant and take extra security measures when using a hot wallet to safeguard your digital assets.
Hot wallets are definitely convenient for accessing cryptocurrency easily, but one must always be cautious about the security risks involved. It’s crucial to choose a reliable provider with strong security measures in place to safeguard your assets effectively.
As a seasoned cryptocurrency expert, I believe that hot wallets offer unparalleled convenience for managing digital assets online. However, it is crucial to prioritize security by choosing reputable providers with robust security measures in place. Remember, always use a hot wallet for everyday transactions and store larger amounts in a cold wallet for added protection against cyber threats.
What are the most common security measures that reputable providers implement for hot wallets? Can you provide examples of top platforms known for their secure hot wallet services?
Reputable providers of hot wallets commonly implement security measures such as two-factor authentication, encryption, and regular security updates to protect users’ digital assets. Examples of top platforms known for their secure hot wallet services include Coinbase, Binance, and Ledger. These platforms prioritize user security and provide robust features to safeguard cryptocurrencies stored in hot wallets.
Could you provide more information on how exactly two-factor authentication works in relation to hot wallet security?
Sure thing, JenniferSmith231! Two-factor authentication adds an extra layer of security to your hot wallet by requiring not only a password and username but also something that only you have on you, such as a piece of information or a physical device. This way, even if someone steals your login credentials, they would still need the second factor to gain access to your account. It significantly enhances the security of your hot wallet and helps protect your cryptocurrencies from unauthorized access. Hope this clarifies it for you!
Hot wallets are indeed convenient for accessing cryptocurrencies easily, but it’s crucial to stay vigilant against potential cyber threats and choose a trusted provider with robust security measures.
Hot wallet crypto is a convenient solution for managing cryptocurrencies online, but users must prioritize security when using it. It’s important to choose a trusted provider with robust security features to safeguard assets from cyber attacks.
Using a hot wallet for cryptocurrency is convenient for quick access, but one must always be cautious about the security risks associated with it. It’s crucial to select a reputable provider with robust security features to safeguard your assets effectively.
Hot wallet crypto provides convenient access to digital assets online, but users must prioritize security when choosing a provider. It’s essential to opt for platforms with robust security features like two-factor authentication and encryption to safeguard against cyber attacks and theft risks.
Hot wallets are indeed convenient for easy access to cryptocurrencies, but users must be cautious about the security risks involved. It is crucial to select a trustworthy provider with robust security features to safeguard your digital assets effectively. Remember, always prioritize safety over convenience when it comes to managing your crypto online.
As an active cryptocurrency trader, I find hot wallets really convenient for quick access to my digital assets. However, it’s crucial to stay vigilant and follow strict security measures to protect against potential cyber threats.
As an experienced crypto enthusiast, I believe that hot wallets indeed offer convenience for quick access to cryptocurrencies, but one must be cautious about the security risks they pose. It’s crucial to choose a reliable provider with robust security features and to limit the amount stored in the hot wallet for enhanced protection against cyber threats.
As an avid user of hot wallet crypto, I appreciate the convenience it offers in accessing my digital assets anywhere. However, it’s important to stay vigilant against cyber threats by choosing a secure provider and implementing extra layers of protection to safeguard against potential risks.
I believe that hot wallets are indeed convenient for quick access to cryptocurrency, but the increased risk of cyber attacks is a major concern. It’s vital to choose a trusted provider with robust security features and be cautious with the amount of digital assets stored in a hot wallet. Balancing convenience with security is key in the world of crypto storage.
Hot wallet crypto provides a convenient way to manage and access cryptocurrencies online, but users need to be cautious about the increased risk of cyber attacks. It’s important to select a trusted provider with robust security features and to store only small amounts in the hot wallet for daily transactions.
Hot wallets offer easy access to cryptocurrencies, but users must remain vigilant about security to protect their assets against cyber threats. It’s crucial to select a trustworthy platform with robust security features in place, such as two-factor authentication and encryption, and to limit the amount stored in a hot wallet for everyday use.
Do you have any recommendations for specific hot wallet providers that offer the best security features? I want to ensure my cryptocurrencies are well-protected.
Sure thing, Emily! When it comes to choosing a hot wallet provider with top-notch security features, you can consider options like Ledger Nano S, Trezor, or Coinbase Wallet. These providers offer robust security measures such as advanced encryption, secure private key storage, and multi-signature authentication to help safeguard your digital assets. Remember to always prioritize security when selecting a hot wallet for your cryptocurrencies.
Hot wallets are great for easy access to your cryptocurrency, but you need to be cautious about security risks. I always make sure to choose a reliable provider that offers strong encryption and two-factor authentication for added protection.
Do hot wallets really provide a secure solution for managing cryptocurrencies online? How can users ensure their assets are protected against cyber attacks?
Hot wallets can offer convenience but also come with increased cybersecurity risks. To protect your assets, opt for reputable providers with robust security features like two-factor authentication and encryption. Consider keeping only small amounts in hot wallets for daily transactions and larger sums in cold wallets for long-term storage.
Hot wallets are a convenient option for accessing cryptocurrencies easily, but users should be cautious about the potential security risks associated with having their assets constantly connected to the internet. It is important to select a trusted provider that prioritizes security features such as two-factor authentication and encryption to safeguard digital assets effectively.
Hot wallets are definitely convenient for accessing cryptocurrencies quickly, but it’s crucial to prioritize security when choosing a provider. Always opt for platforms with robust security features to safeguard your assets from potential cyber threats.
Hot wallets are really convenient for accessing cryptocurrencies on the go, but it’s important to stay vigilant against cyber threats. As long as you choose a trustworthy provider with robust security features, using a hot wallet can be a practical solution for managing your digital assets online.
As an active cryptocurrency user, I believe hot wallets offer great convenience for daily transactions. However, it is crucial to stay updated on security measures and use them wisely to avoid potential risks associated with online hacking.
Hot wallet crypto is a convenient solution for accessing and managing cryptocurrencies online, but users must prioritize security when using such wallets. It is vital to select a trusted provider that implements robust security measures to safeguard digital assets effectively. Remember, with great accessibility comes great responsibility in protecting your funds in the digital realm.
Do hot wallets really provide a secure solution for storing cryptocurrencies online? How can users best protect their assets from potential cyber attacks while using a hot wallet?
Yes, hot wallets offer a convenient way to store and access cryptocurrencies online. To enhance security, users should opt for reputable providers with robust security measures such as two-factor authentication and encryption. Keeping only small amounts in the hot wallet for daily transactions and larger sums in a cold wallet for long-term storage is a wise practice to safeguard your assets from cyber threats.
Hot wallets are indeed convenient for quick access to cryptocurrencies, but it’s crucial to always prioritize security. Choosing a reliable provider with robust security features is paramount to safeguarding your digital assets from potential cyber threats.
As an avid crypto investor, I believe that hot wallets are convenient for quick transactions but require extra vigilance due to the increased risk of cyber attacks. It’s crucial to choose a reliable provider with top-notch security features to safeguard your digital assets.
Hot wallets are definitely convenient for easy cryptocurrency access, but it’s crucial to remember the security risks involved. Always opt for platforms with robust security features and consider keeping larger amounts in a cold wallet for added protection.
I believe hot wallets can be very useful for daily transactions. However, I always recommend using them with caution. The convenience is great, but it’s vital to prioritize security. I only keep a small amount in my hot wallet and store the rest in a cold wallet. Staying safe in the crypto world is a top priority!
Thanks for the informative article! I’m curious, what specific security measures should I look for in a hot wallet provider to ensure my assets are protected?
Hi SarahTech89! Great question! When selecting a hot wallet provider, look for features like two-factor authentication, end-to-end encryption, and a strong track record of security. Regular security updates and a good customer support team are also crucial. Always do your research before entrusting your assets to anyone!
I really appreciate the convenience of hot wallets for transactions, but I always feel a bit uneasy about their security. It’s so important to choose a reliable provider and be cautious with how much crypto we keep in them. A mixed strategy with both hot and cold wallets seems like the best way to go!
I personally prefer using hot wallets for their convenience, especially for small transactions. However, I always ensure that I’m using a reputable provider and follow the best practices to keep my assets safe. The ease of access on various devices is a huge plus, but I totally understand the risks involved. Balancing security and convenience is key!
I believe hot wallets are great for convenience, especially for those who make frequent transactions. However, the security risks are definitely a concern. It’s important to choose a reputable provider and stay cautious about the amounts you keep in there. Balancing convenience and security is key!
I think hot wallets offer great convenience, especially for frequent traders. However, I always make sure to keep only small amounts in them due to the risks involved. Security should definitely be a priority; it’s essential to pick a trustworthy platform. Balancing accessibility with safety is key!
Great article! I’m curious, what are some of the best practices you recommend for keeping my hot wallet secure?
Thanks, Jessica! To keep your hot wallet secure, I recommend using strong, unique passwords and enabling two-factor authentication wherever possible. Also, make sure to regularly update your wallet software and be cautious of phishing attempts. Stay safe out there!
I think hot wallets are great for those who need quick access to their crypto, but honestly, I wouldn’t keep a lot of funds in one. The risk of hacking is just too high for larger amounts. It’s definitely essential to take the right precautions if you choose to use one. Strong security measures are a must!
I think hot wallets are a great option for those who frequently trade and need quick access to their digital assets. However, I’ve noticed that many users underestimate the risks involved. It’s essential to stay aware of security measures, like enabling two-factor authentication and keeping only small amounts in these wallets. Balancing convenience and security is key!
I believe that hot wallets are great for those who want quick access to their funds, but it’s important to stay cautious. The convenience they offer is undeniable, but I always recommend using them for small amounts. Keeping a significant amount in a cold wallet is definitely a smarter choice for security. Always prioritize safety!